HOW TO PROTECT YOURSELF ONLINE
Safeguard your digital profile against cybercrimes with these tips from the National Cyber Security Alliance (staysafeonline.org)
Download Our Cyber Security Guide
{beginNavtabs}
Cyber Security
As part of our ongoing efforts to protect you and your accounts from potential cyber threats, we want to share some important information and tips to help you stay safe in the digital world.
5 Tips for Cyber Security
- Strong Passwords: Create complex, unique passwords for each of your online accounts. Use a combination of upper and lower-case letters, numbers, and special characters. Avoid using easily guessable information like birthdays or names. The longer they are the better. Passphrases are great when supported. For example, “I love Keystone Bank!”.
- Two-Factor Authentication (2FA) and Device Security: Enable 2FA wherever possible. This can be a text message with a code, or an application like Google Authenticator, Microsoft Authenticator, or DUO to name a few. This adds an extra layer of security by requiring a second verification step and can stop identity thieves in their tracks. Always secure your devices with passcodes, PINs, or biometric authentication. This adds a layer of protection in case they are lost or stolen.
- Beware of Phishing or Business Email Take-Over: Be cautious of unsolicited emails, messages, or calls that request personal or financial information. Legitimate organizations will never ask for sensitive data or usernames and passwords via email or text. Be on the lookout for strange email addresses, attachments you weren’t expecting, bad spelling, or “emergencies” that request money right away. Always verify the authenticity of any unusual or unexpected instructions received via email with a simple phone call to the sender, especially when they involve financial transactions or sensitive data.
- Keep Software Updated: Regularly update your computers and phones to the latest operating systems and applications. These updates often include security patches that address known vulnerabilities.
- Public Wi-Fi: Avoid using public Wi-Fi for sensitive transactions. Data thieves are known to sit in places like your favorite coffee shop and monitor all the computer traffic on the public WI-FI looking for usable information. If you must work in a public space, use a VPN to encrypt your data.
Our Commitment to You
Keystone Bank takes your security seriously. We employ advanced security measures to protect your accounts and transactions, and we monitor for unusual activity. However, your vigilance is also essential in this partnership. By following the above tips and staying informed, you can help us ensure your financial security.
If you ever suspect any fraudulent activity related to your Keystone Bank account, please contact us immediately. Your prompt action can help prevent potential losses.
Check Fraud
Check Fraud
Instances of sophisticated check fraud are on the rise. Criminals are using advanced methods to steal, alter, or counterfeit checks, taking advantage of weaknesses in the check clearing process. It's crucial to be informed and equipped to prevent falling victim to these fraudulent activities. To bolster your protection against check fraud and related risks, we strongly recommend two proactive measures:
- Positive Pay
This powerful fraud prevention tool allows you to notify us about the checks you have written. When these checks are presented for clearing, we cross-reference them against your provided information. If any discrepancies are detected, we will contact you for verification before processing the transaction. This extra layer of security helps prevent unauthorized checks from clearing your account. - ACH Origination
Electronic payment methods, such as Automated Clearing House (ACH) origination, offer a secure and efficient alternative to traditional paper checks. By adopting ACH origination, you can minimize the risk associated with physical checks and enjoy quicker, traceable payments.
We strongly encourage you to take the following steps to enhance your account security:
- Enroll in Positive Pay - To get started with Positive Pay, please reach out to our customer support team at 888-266-9707.
- Explore Electronic Payment Methods - Consider utilizing ACH origination and other electronic payment options for a more secure and streamlined transaction experience.
- Stay Vigilant - Regularly review your account statements and transaction history for any unusual or unauthorized activity. Banks have strict regulatory timelines to return a check that you don’t recognize, so it’s imperative that you monitor your accounts daily and if you notice anything suspicious, contact us immediately.
Protect Yourself
Own It
- Never click and tell. Limit the personal information you share on social media platforms, including the use of location services.
- Keep tabs on your apps. Only download apps from trusted vendors and sources. Review app permissions to ensure default permissions are not set to run in the background.
Secure It
- Shake up your password protocol. Avoid using standard passwords or phrases across multiple websites. Consider using a password manager to generate and store unique and complex logins for each of your accounts.
- Double your login protection. Enable multi-factor authentication (MFA) when available.
- Play hard to get with strangers. Do not respond to or click on the links or attachments of “phishy” emails.
Protect It
- If you connect, you must protect. Maintain the most up-to-date security software, web browser, operating system, and antivirus software (if available) to protect your computer, smartphone, game device, or other network device.
- Stay protected while connected. Refrain from conducting sensitive activities, such as banking, when connected to a public Wi-Fi network.
Account Takeover
HOW TO AVOID ACCOUNT TAKEOVER FRAUD
What is an “account takeover”?
An account takeover happens when a fraudster poses as a financial institution to get your personal or account information. Once the fraudster has access to your account, they can make unauthorized transactions.
|
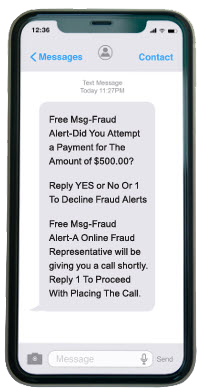
How Does It Work? An account takeover begins with a fraudster sending a text message to your mobile phone. They usually claim they‘re from a financial institution‘s fraud department. They ask you to confirm a suspicious payment that was sent from your account — this may not be true and could be part of the fraud. If this is a fraud attack, the fraudster typically follows up with a phone call and asks for your personal information to “cancel the payment.” NOTE: we will NEVER ask for your personal information over the phone. While account takeover fraud attempts can happen at anytime, it usually begins on a Friday, after business hours, and runs through the weekend. The phone shows an example of a fraudulent “account takeover” text message. |
How Can You Prevent Account Takeover Fraud?
| If someone posing as contacts you by phone, email, or text message and wants you to share your personal information, consider it fraud. | |
| If you receive a text (or email) like the one shown here, do not reply to the sender. Ignore the message and do not call any phone numbers listed in the text. | |
| If you receive a phone call that seems to be a phishing attempt, end the call immediately. And be aware that area codes can be misleading: a local area code does not always guarantee that the caller is local. |
Protect Your Business
PROTECT YOUR BUSINESS
What is an “Corporate Account Takeover”?
Corporate Account Takeover (CATO) is a form of business identity theft where criminals gain control of a business’ bank account by stealing employee passwords and other valid credentials. Malicious actors can then initiate fraudulent wire and ACH transactions to accounts they control.
What is “Business Email Compromise”?
Business Email Compromise (BEC) is a sophisticated scam targeting businesses working with foreign suppliers and/or businesses that regularly perform wire transfer payments. The scam is carried out by compromising legitimate business email accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds. This includes compromising the business email accounts of a company’s vendors and/or customers.
|
What to look out for:
Best Practices:
|
What to do if you fall victim to fraud:
|
Zelle Security
You already know Zelle® is a fast, safe and easy way to send money to people you know and trust. With that in mind, it’s important to remember to “pay it safe.”
Here are three tips to help you 'pay it safe' with Zelle®:
Only send money to people you know and trust.
Money moves fast with Zelle®. Directly from bank account to bank account within minutes.* So, it's important you know and trust people you're sending money to. You can't cancel a payment once it's been sent if the recipient is already enrolled with Zelle®, so it's important to get it right the first time.
Beware of payment scams.
If you send money to someone you don't know for a product or service you might not receive (like paying for something in advance), you may not get your money back.
Treat Zelle® like cash.
Money moves fast - directly into the enrolled recipient's bank account. Make sure you're sending to the right person by confirming the first name displayed is that of your recipient.
To learn more about using Zelle® safely, review this guide.
{endNavtabs}